- Users are required to access to Cloud Defense Account
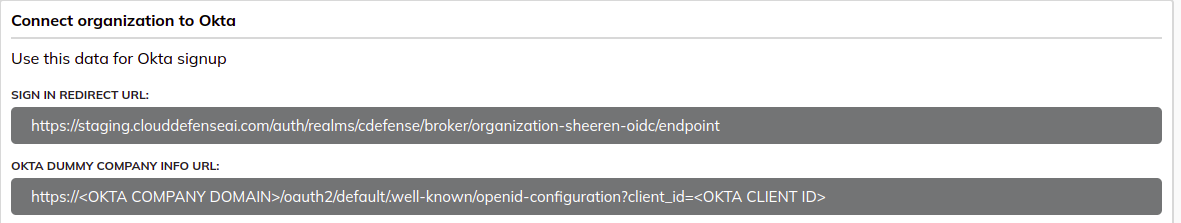
Before creating an APP in OKTA, first login to Cloud Defense. Inside the Integrations tab, go to SSO, click on OKTA and copy the redirect URL.
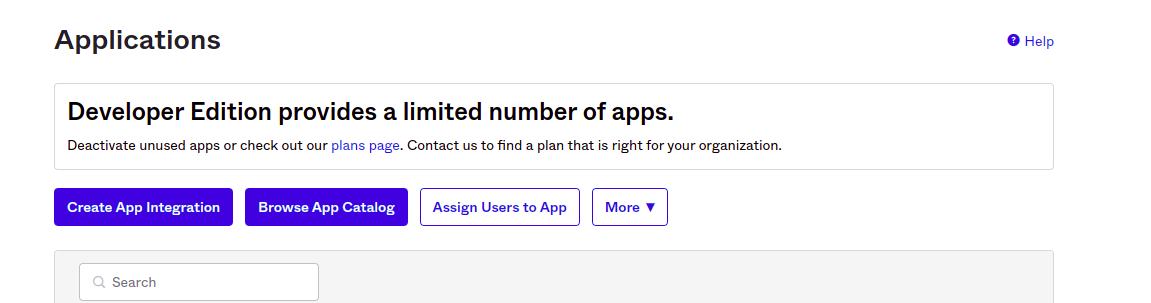
Go to the applications page in OKTA, and click on Create App Integration.
Select Open-id connect as sign in method, and web application as Application

In General Settings, enter App name, select Grant type as Client credentials and Authorization code as Client acting on half of a user, enter the redirect url copied from Cloud defense application, and paste it in redirect URLs.





Fix- Check the client id and client secret. Most probably the issue will be with credentials, if other IDPs are working. In case all IDPs are not working and showing the same issue, then we can probably look at ingress logs. https://stackoverflow.com/questions/42613491/azure-ad-webapp-behind-reverse-proxy-receives-502-bad-gateway
This error comes when we add the first login flow in identity provider settings as Linking Broker Flow. This error comes when we try to login with a new identity provider and email already exists with some other identity provider. In this case the below API fails and in the events we receive
IDENTITY_PROVIDER_FIRST_LOGIN_ERROR
https://staging.clouddefenseai.com/auth/realms/cdefense/login-actions/first-broker-login?client_id=cdconsole&tab_id=oThe first step to debug this issue is to check the linking broker flow settings inside the authentication tab. Make sure if Create User If Unique and Automatically Set Existing User both are set to Alternative. Also check if both are added in the same order mentioned above.


Make sure the correct frontend url is added in the realm settings as shown in screenshot 1. This is the frontend Url of our realm.
Also, in the clients section, select cdconsole and make sure Root URL, Valid Redirect URIs and Base URL are added correctly as mentioned in screenshot 2.
In order to fix this error, please update the type of value column in user_attribute table as text. This will solve this error.
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article