Log in to Cloud Security portal using your credentials : https://acs-us.clouddefenseai.com/ 

- Using CloudFormation Template
Prerequisites:
- Make sure the AWS IAM user you'll use to create the CloudFormation Stack has the following permissions attached - AmazonSNSFullAccess, AWSCloudFormationFullAccess and IAMFullAccess.
Step 1: Choose to add single/multiple AWS Account(s)
Select whether you want to connect a single AWS account or onboard multiple accounts at once for centralized visibility and management.

Step 2: Enter Account ID
Provide the unique 12-digit AWS account ID to identify and link your AWS account with the platform securely.
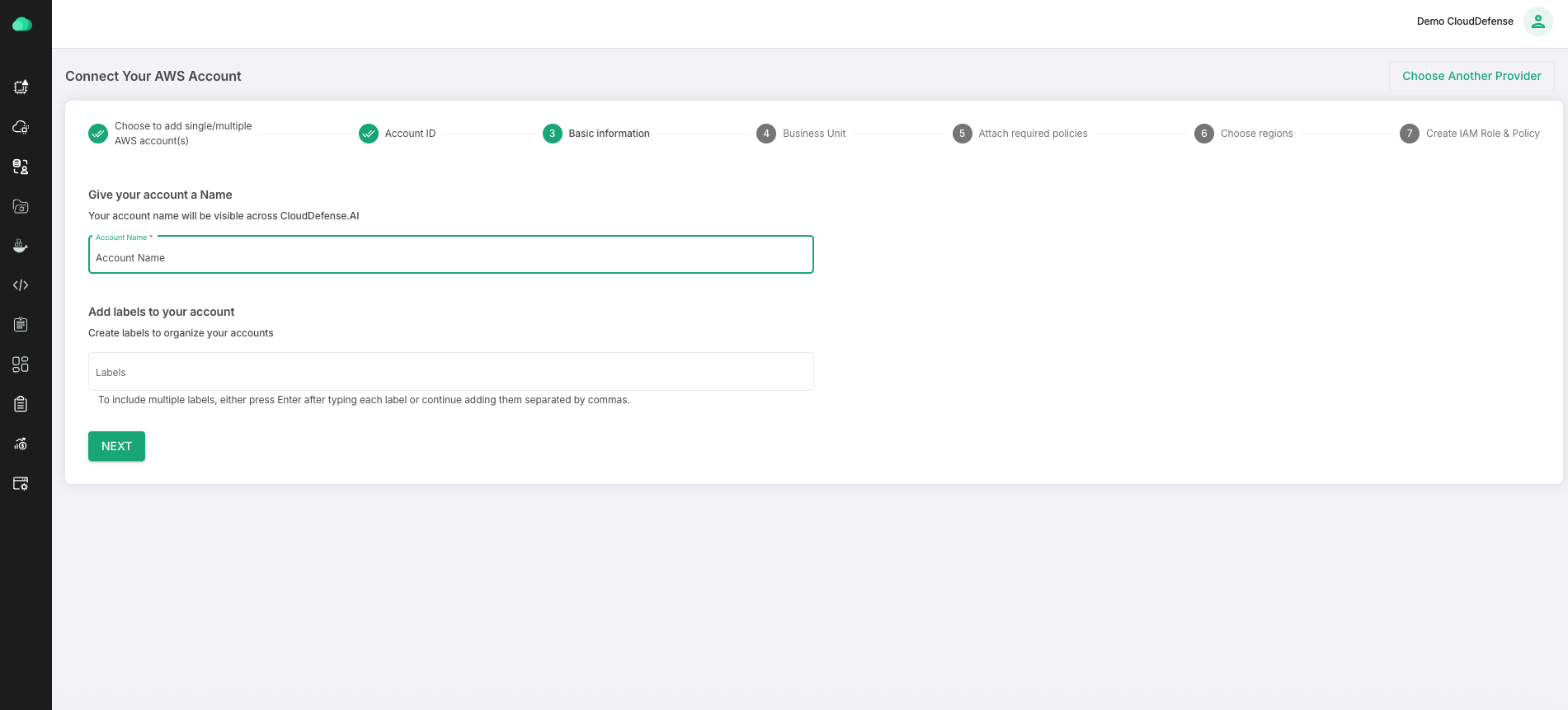
Start with giving it a name. You can give any name for your account. Labels help you to identify the account. Some examples of labels are: US PROD, Dev server, etc.
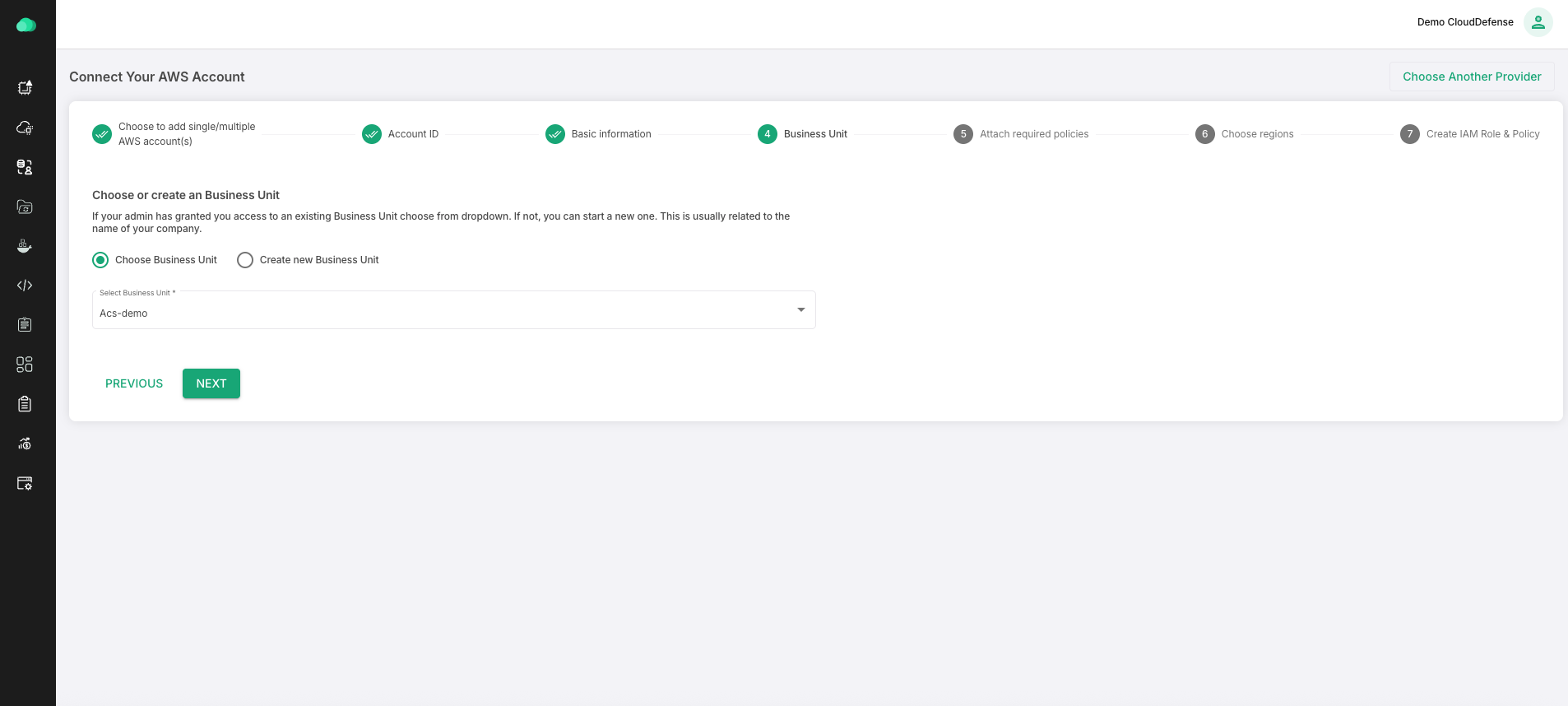
Select or create a existing business unit to add new account into. An Business Unit is where you can add multiple AWS accounts.
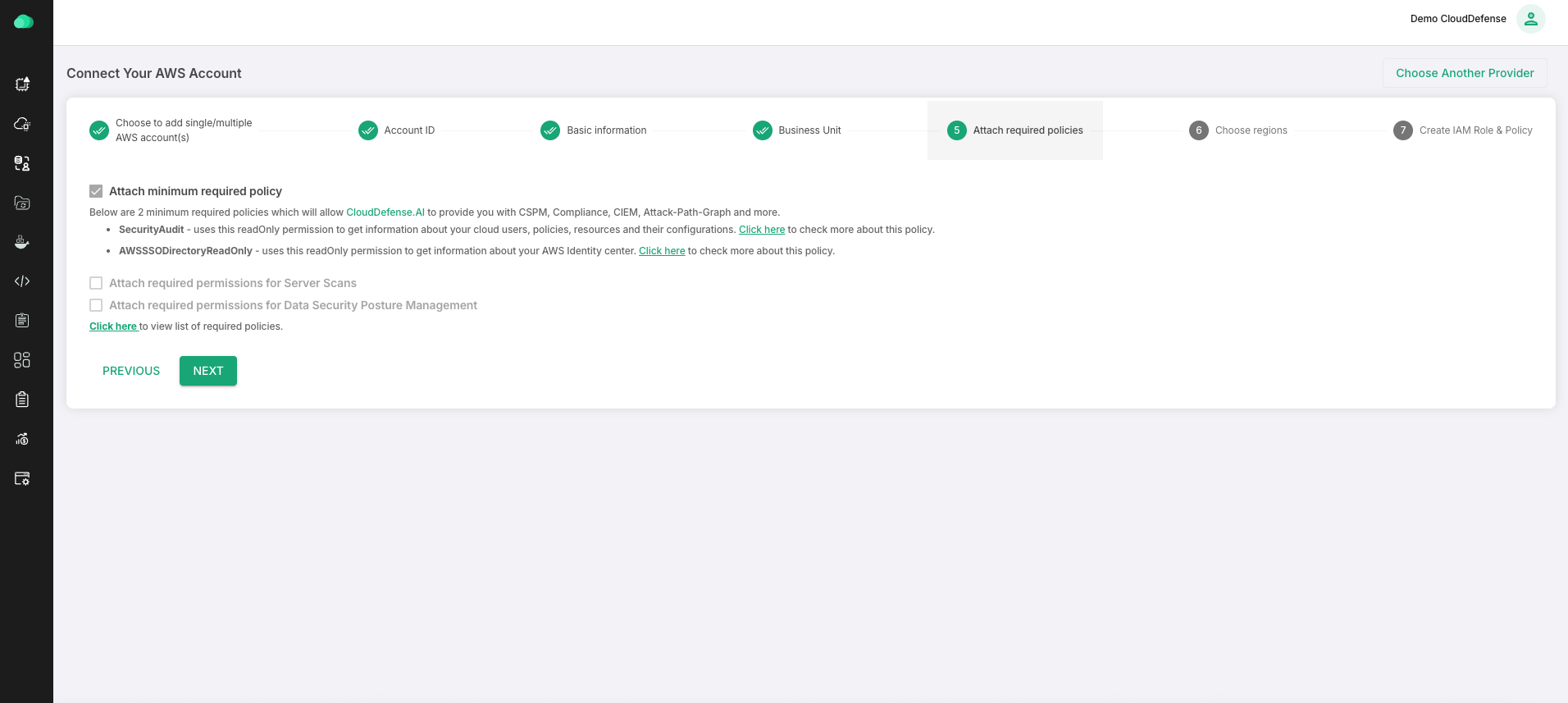
This is where you need to decide on the policies. You will see 3 checkboxes there:
- Minimum required policy: This is the minimum required policy (read-only) we would need to evaluate your resources. We will attach SecurityAudit, AWSSSODirectoryReadOnly policy along with custom inline policy attached below to get information about your cloud users, policies, resources, and their configurations and Identity store data. This helps us to provide you with CSPM, Compliance, CIEM, Attack-Path-Graph, and more. To check what actions can be performed by CloudDefense if this policy is attached, Click here
OtherRequiredPolicies{
"PolicyName": "OtherRequiredReadOnlyPermissions",
"PolicyDocument": {
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"macie2:ListClassificationJobs",
"waf:ListRuleGroups",
"backup:ListProtectedResources",
"lambda:GetFunctionUrlConfig",
"backup:GetBackupSelection",
"backup:ListBackupPlans",
"backup:ListBackupSelections",
"waf:ListRules",
"backup:ListRecoveryPointsByBackupVault"
],
"Resource": "*"
}
]
}
}
- Required permissions for Workload Scan: Below is the list of required permissions. A custom policy having these actions will be attached to CloudFormation Stack.
- ssm:SendCommand
- ssm:StartSession
- ssm:CancelCommand
- ssm:ListCommandInvocations
- ssm:TerminateSession
- ssm:GetCommandInvocation
We will only scan the regions that you choose here. You can choose any specific region or all regions. This selection can be changed later.

Please review the details of the generated CloudFormation policy by clicking on the hyperlink on this page.

On the AWS screen, follow the steps to finishing adding CloudFormation policy:
- Click check box “I acknowledge that AWS CloudFormation might create IAM resources with custom names.“(Refer to image below)
- Click Create Stack button. (Refer to image below)

AWS Resource Creation while onboarding
As part of the onboarding process with CloudDefense.AI, the following AWS resources will be created in your AWS account to enable monitoring and integration with CloudDefense.AI:
Resources to Be Created:
1. EventBridge IAM Role:
This IAM role will be created to enable communication between your AWS environment and CloudDefense.AI. The role will notify CloudDefense.AI when all the necessary resources are successfully created in your AWS environment. This ensures that the onboarding process is complete and that the monitoring setup is ready to function.
A dedicated IAM role will be created to allow CloudDefense.AI to retrieve metadata from your cloud services. This role is essential for continuous monitoring and allows CloudDefense.AI to gather the necessary details about your cloud resources (such as EC2 instances, S3 buckets, RDS instances, etc.) to provide comprehensive security insights and recommendations.
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article