CloudDefense.AI Azure Subscription/Management Group Onboarding Process
This guide provides the simple steps required to connect your Azure subscription to the platform.
Prerequisites
To run the automated onboarding script, the Azure account you use for az login must have permissions to:
Create new Azure AD applications (Service Principal).
Create a Custom Role definition.
Assign that new Custom Role at the subscription level.
Platform Access and Permissions
The onboarding process grants the platform read-only access to your subscription.
The script automatically creates a Service Principal (Application) and assigns it a Custom Role with permissions to read security-relevant resources, including:
All Resources: Read access to inventory in the subscription (*/read).
Key Vaults: These permissions allow read-only visibility into Azure Key Vault operations and configurations — including checking vault name availability, viewing deleted vaults, retrieving vault details and regional metadata, and listing supported management operations — without granting access to stored secrets, keys, or certificates.
Storage Accounts: This permission enables to view and retrieve only access keys associated with an Azure Storage Account.
App Services: Permissions to list configuration settings and connection strings.
Log in to Cloud Security portal using the link received in email from us to complete the registration process and login.

Once you successfully logged in for the first time. You will be able to see the "Environment" page only under Global Tenant Setting (please refer to the screenshot below). 
CloudDefense.AI Azure Single Subscription Onboarding Process
Prerequisites
User Who will be proceeding with addition of app registration and allocation of role to app must have below permission:
1. Azure Entra ID level Access :
- Global Administrator
Owner
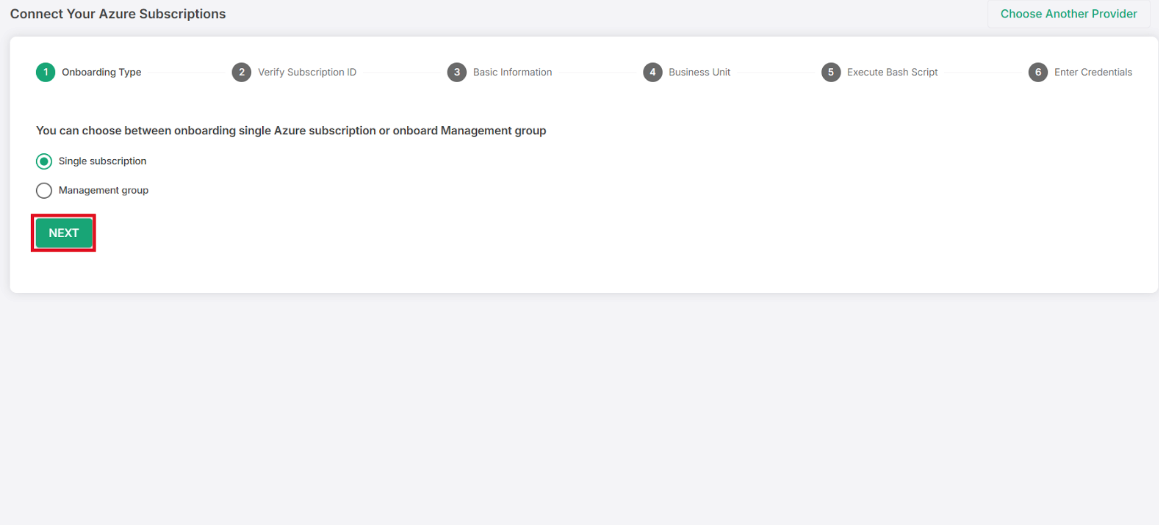
STEP 1. Select Onboarding Type
Ensure Single subscription is selected (or choose Management group if applicable).
Click NEXT.
STEP 2. Verify Subscription ID
Enter the Subscription ID for the Azure account you wish to onboard.
Click Verify.

STEP 3: Provide Basic Information
Enter a memorable Account Name (e.g., Azure Onboarding).
(Optional) Add any organizational Labels.
Click NEXT.

STEP 4: Define Business Unit
Select whether to Choose Business Unit from a dropdown or Create new Business Unit.
Enter the New Business Unit Name (e.g., azure-accounts).
Click NEXT.

STEP 5: Generate and Execute Bash Script
Review the Subscription ID displayed and click Generate Script.
Action required in Azure Cloud Shell or local environment:
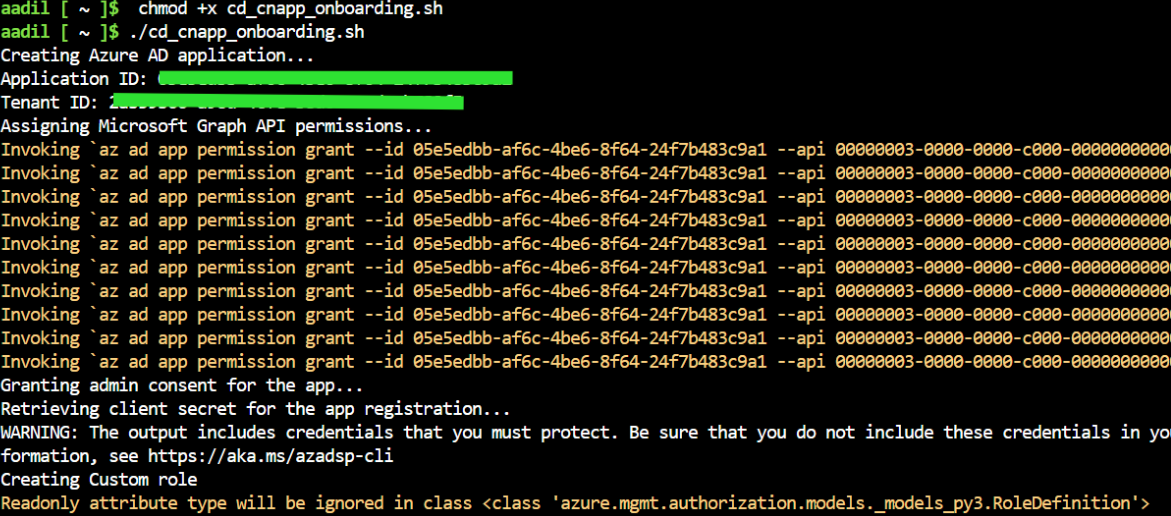
You will need to run the generated script. Before executing the script, ensure you are logged into Azure with az login using an account that has permission to create resources in the target subscription.
Execute the script (e.g., ./cd_cnapp_onboarding.sh).
The script will create the necessary Azure AD application, assign permissions, and output the required credentials in your terminal.


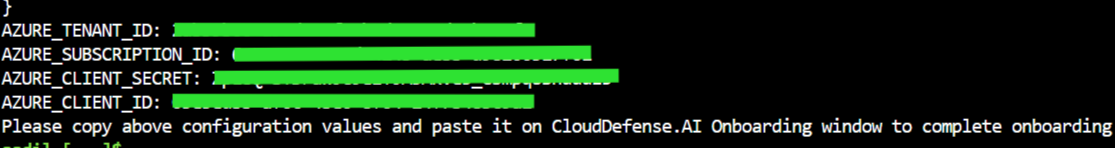
STEP 6: Enter Credentials
From the script output in your terminal, copy the four credential values:
AZURE_CLIENT_ID
AZURE_CLIENT_SECRET
AZURE_SUBSCRIPTION_ID
AZURE_TENANT_ID
Paste these values into the corresponding fields on the platform.

For CSPM and CIEM Module – Following are the permissions required by the created applications along with the custom role.
1) Graph permissions to be attached to the App
- Application.Read.All
- AuditLog.Read.All
- Directory.Read.All
- Domain.Read.All
- Group.Read.All
- IdentityProvider.Read.All
- Policy.Read.All
- User.Read.All
- Reports.Read.All
2) Custom built role with below role definition will get attached to the app for subscription
{
"properties": {
"roleName": "ReadOnlyCustomRole",
"description": "A custom role to view all resources, but does not allow you to make any changes in the infrastructure.",
"assignableScopes": [
"/subscriptions/{subscriptionId}"
],
"permissions": [
{
"actions": [
"*/read",
"Microsoft.KeyVault/checkNameAvailability/read",
"Microsoft.KeyVault/deletedVaults/read",
"Microsoft.KeyVault/locations/*/read",
"Microsoft.KeyVault/vaults/*/read",
"Microsoft.KeyVault/operations/read",
"Microsoft.Web/sites/config/list/action",
"Microsoft.Storage/storageAccounts/listKeys/action",
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}
CloudDefense.AI Azure Management Group Onboarding Process
Prerequisites
User Who will be proceeding with addition of app registration and allocation of role to app must have below permission:
1. Management Group level Access :
- Owner
- Global Administrator
STEP 1:
Login to CloudDefense portal using your credentials.

From the Sidebar, navigate to Admin -> Environments.
Now Click on Add New Environment and then choose Microsoft Azure provider as below.

STEP 2:
Select Management Group option if you wish to onboard your Azure management group.

STEP 3:
Now select your Organization from the drop down menu and click next.

STEP 4:
Enter your Azure Management Group ID in the given input box.

#!/bin/bash
SP_NAME="CDAI Service Principal"
MANAGEMENT_GROUP_NAME="dddd3d67-fe87-4bca-a99e-d03d289df91e"
# Create Custom role at Management Group
echo "Creating Custom role at management group scope"
az role definition create --role-definition '{"Name":"CDAIReadOnlyCustomRole","IsCustom":true,"Description":"A custom role to view all resources within a management group, but does not allow to make any changes in the infrastructure.","Actions":["*/read","Microsoft.KeyVault/checkNameAvailability/read","Microsoft.KeyVault/deletedVaults/read","Microsoft.KeyVault/locations/*/read","Microsoft.KeyVault/vaults/*/read","Microsoft.KeyVault/operations/read"],"NotActions":[],"AssignableScopes":["/providers/Microsoft.Management/managementGroups/dddd3d67-fe87-4bca-a99e-d03d289df91e"]}'
sleep 10
# Create Service Principal at Management Group scope
echo "Creating service principal at management group level"
SP_OUTPUT=$(az ad sp create-for-rbac --role "CDAIReadOnlyCustomRole" --scopes /providers/Microsoft.Management/managementGroups/dddd3d67-fe87-4bca-a99e-d03d289df91e --name "$SP_NAME")
APP_ID=$(echo $SP_OUTPUT | jq -r '.appId')
CLIENT_SECRET=$(echo $SP_OUTPUT | jq -r '.password')
TENANT_ID=$(echo $SP_OUTPUT | jq -r '.tenant')
# Add existing Microsoft Graph permissions
GRAPH_API_ID=$(az ad sp list --filter "displayName eq 'Microsoft Graph'" --query '[0].appId' -o tsv)
echo "Assigning Microsoft Graph API permissions..."
PERMISSIONS=(
"9a5d68dd-52b0-4cc2-bd40-abcf44ac3a30=Role"
"b0afded3-3588-46d8-8b3d-9842eff778da=Role"
"7ab1d382-f21e-4acd-a863-ba3e13f7da61=Role"
"dbb9058a-0e50-45d7-ae91-66909b5d4664=Role"
"5b567255-7703-4780-807c-7be8301ae99b=Role"
"246dd0d5-5bd0-4def-940b-0421030a5b68=Role"
"230c1aed-a721-4c5d-9cb4-a90514e508ef=Role"
"c7fbd983-d9aa-4fa7-84b8-17382c103bc4=Role"
"df021288-bdef-4463-88db-98f22de89214=Role"
"38d9df27-64da-44fd-b7c5-a6fbac20248f=Role"
)
for perm in "${PERMISSIONS[@]}"; do
IFS='=' read -r PERMISSION TYPE <<< "$perm"
az ad app permission add --id $APP_ID --api $GRAPH_API_ID --api-permissions $PERMISSION=$TYPE
done
echo "Granting admin consent for the app..."
az ad app permission admin-consent --id $APP_ID
# Fetch all subscriptions under Management Group
echo "Here is the list of Subscription IDs to be uploaded"
for sub in $(az account management-group subscription show-sub-under-mg --name dddd3d67-fe87-4bca-a99e-d03d289df91e --query "[?inheritedPermissions!='noaccess' && permissions!='noaccess'].{Id:id}" -o tsv | tr '/' ' ' | cut -d ' ' -f 7); do
echo "$sub"
done
echo "AZURE_TENANT_ID: $TENANT_ID"
echo "AZURE_CLIENT_SECRET: $CLIENT_SECRET"
echo "AZURE_CLIENT_ID: $APP_ID"Please copy above configuration values and paste it on CloudDefense.AI Onboarding window to complete onboarding"
STEP 5:
Copy appId value from above command result & paste in Client ID input box
Copy secret value from above command result & paste in Client Secret input box
Copy tenant value from above command result & paste in Tenant ID input box
Get all the list of subscriptions and paste them into the given input box.

Now, just click on Connect Management Group and your onboarding is complete!
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article